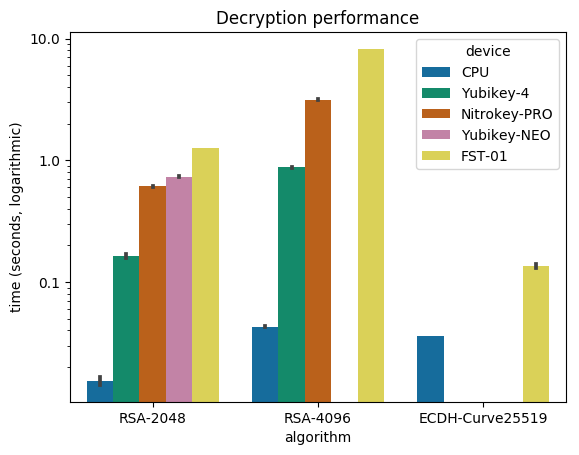
In June I travelled to see Nine Inch Nails perform two nights at the
Eden
Project in Cornwall. It'd been
eight
years since I last saw them live and when they announced
the Eden shows, I thought it might be the only chance I'd get to see them for a
long time. I committed, and sods law, a week or so later they announced a
handful of single-night UK club shows. On the other hand, on previous tours
where they'd typically book two club nights in each city, I've attended one
night and always felt I should have done both, so this time I was making that
happen.
Newquay

approach by air

Towan Beach (I think)
For personal reasons it's been a difficult year so it was nice to treat
myself to a mini holiday. I stayed in Newquay, a seaside town with many
similarities to the North East coast, as well as many differences. It's
much bigger, and although we have a thriving surfing community in Tynemouth,
Newquay have it on another level. They also have a lot more tourism, which
is a double-edged sword: in Newquay, besides surfing, there was not a lot
to do. There's a
lot of tourist tat shops, and bars and cafes (som very
nice ones), but no book shops, no record shops, very few of the quaint,
unique boutique places we enjoy up here and possibly take for granted.
If you want tie-dyed t-shirts though, you're sorted.
Nine Inch Nails have a long-established, independently fan-run forum
called
Echoing The Sound. There is
now also an official Discord server. I asked on both whether anyone was
around in Newquay and wanted to meet up: not many people were! But I did
meet a new friend, James, for a quiet drink. He was due to share a taxi
with Sarah, who was flying in but her flight was delayed and she had to
figure out another route.
Eden Project

the Eden Project
The Eden Project, the venue itself, is a fascinating place. I didn't realise
until I'd planned most of my time there that the gig tickets granted you free
entry into the Project on the day of the gig as well as the day after. It was
quite tricky to get from Newquay to the Eden project, I would have been better
off staying in St Austell itself perhaps, so I didn't take advantage of this,
but I did have a couple of hours total to explore a little bit at the venue
before the gig on each night.
Friday 17
th (sunny)
Once I got to the venue I managed to meet up with several names from ETS and
the Discord: James, Sarah (who managed to re-arrange flights), Pete and his
wife (sorry I missed your name), Via Tenebrosa (she of crab hat fame), Dave
(DaveDiablo), Elliot and his sister and finally James (sheapdean), someone who
I've been talking to online for over a decade and finally met in person (and
who taped both shows). I also tried to meet up with a friend from the Debian
UK community (hi Lief) but I couldn't find him!
Support for Friday was
Nitzer Ebb, who I wasn't familiar with before. There
were two men on stage, one operating instruments, the other singing. It was a
tough time to warm up the crowd, the venue was still very empty and it was very
bright and sunny, but I enjoyed what I was hearing. They're definitely on my
list. I later learned that the band's regular singer (Doug McCarthy) was unable
to make it, and so the guy I was watching (Bon Harris) was standing in for full
vocal duties. This made the performance (and their subsequent one at Hellfest
the week after) all the more impressive.

Via (with crab hat), Sarah, me (behind). pic by kraw
(Day) and night one, Thursday, was very hot and sunny and the band seemed a
little uncomfortable exposed on stage with little cover. Trent commented as
such at least once. The setlist was eclectic: and I finally heard some of my
white whale songs. Highlights for me were
The Perfect
Drug, which was unplayed from 1997-2018 and has now become a staple, and the
second ever performance of
Everything, the first being a few days earlier.
Also notable was three cuts in a row from the last LP,
Bad Witch,
Heresy
and
Love Is Not Enough.
Saturday 18
th (rain)

with Elliot, before
Day/night 2, Friday, was rainy all day. Support was
Yves Tumor, who were
an interesting clash of styles: a Prince/Bowie-esque inspired lead clashing
with a rock-out lead guitarist styling himself similarly to Brian May.
I managed to find Sarah, Elliot (new gig best-buddy), Via and James (sheapdean)
again. Pete was at this gig too, but opted to take a more relaxed position than
the rail this time. I also spent a lot of time talking to a Canadian guy on a
press pass (both nights) that I'm ashamed to have forgotten his name.
The dank weather had
Nine Inch Nails in
their element. I think night one had the more interesting setlist, but night
two had the best performance, hands down. Highlights for me were mostly a
string of heavier songs (in rough order of scarcity, from common to rarely
played):
wish,
burn,
letting you,
reptile,
every day is exactly the
same,
the line begins to blur, and finally,
happiness in slavery, the
first UK performance since 1994. This was a crushing set.
A girl in front of me was really suffering with the cold and rain after waiting
at the venue all day to get a position on the rail. I thought she was going to
pass out. A roadie with NIN noticed, and came over and gave her his jacket. He
said if she waited to the end of the show and returned his jacket he'd give her
a setlist, and true to his word, he did. This was a really nice thing to happen
and really gave the impression that the folks who work on these shows are caring
people.

Yep I was this close

A fuckin' rainbow! Photo by "Lazereth of Nazereth"

Afterwards
Night two did have some gentler songs and moments to remember: a re-arranged
Sanctified (which ended a nineteen-year hiatus in 2013)
And All That Could
Have Been (recorded 2002, first played 2018),
La Mer,
during which the rain broke and we were presented with a beautiful pink-hued
rainbow. They then segued into
Less Than, providing the comic moment of the
night when Trent noticed the rainbow mid-song; now a meme that will go down
in NIN fan history.
Wrap-up
This was a blow-out, once in a lifetime trip to go and see a band who are at
the top of their career in terms of performance. One problem I've had with NIN
gigs in the past is suffering gig flashback to them when I go to other
(inferior) gigs afterwards, and I'm pretty sure I will have this problem again.
Doing both nights was worth it, the two experiences were very different and
each had its own unique moments. The venue was incredible, and Cornwall is
(modulo tourist trap stuff) beautiful.
 In June I travelled to see Nine Inch Nails perform two nights at the
In June I travelled to see Nine Inch Nails perform two nights at the 








 As a followup to the previous post, here's an update on the iOS
14 USB tethering problem on Linux. After some investigation, Matti
Vuorela
As a followup to the previous post, here's an update on the iOS
14 USB tethering problem on Linux. After some investigation, Matti
Vuorela