Matthew Garrett: Asking ChatGPT to write my security-sensitive code for me
 I have a patchset that makes it safe to use hibernation under Linux even in a secure boot world but it relies on preventing userland from using one of the TPM PCRs[1] that would otherwise be available to it. TPM 2 devices support emulating PCRs in NVRAM, which would obviously be beneficial in not taking away a scare resource, but the docs suggest there's no way to tie a key generation to an NVRAM value which makes this more complicated.
I have a patchset that makes it safe to use hibernation under Linux even in a secure boot world but it relies on preventing userland from using one of the TPM PCRs[1] that would otherwise be available to it. TPM 2 devices support emulating PCRs in NVRAM, which would obviously be beneficial in not taking away a scare resource, but the docs suggest there's no way to tie a key generation to an NVRAM value which makes this more complicated.So, why not ask a computer to do this for me? I asked ChatGPT to write me some code that would bind a TPM key to an NVRAM value. After a couple of false starts it told me:
To bind an encryption key to the value of a TPM NV index, you can use the TPM2_NV_DefineSpace command to define an NV index with the TPMA_NV_BIND attribute.Woo! That sounds perfect. Only one problem - I can't actually find the TPMA_NV_BIND attribute defined anywhere in the spec. Well, ask the AI again.
Here is the definition of TPMA_NV_BIND from the TPM 2.0 specification:
TPMA_NV_BIND (BIT 17) If SET, the contents of the NV Index are bound to the platform hierarchy.
Ok, that sounds convincing. Where is it in the spec?
The definition of TPMA_NV_BIND is on page 126 of the TPM 2.0 specification, in section 9.7.1 "TPMA_NV".
Huh. Nope. Page 126 says nothing about this. Section 9.7.1 says nothing about this. The TPMA_NV bits are actually described on page 168 of volume 2 of the spec, in section 13.4. Bit 17 is TPMA_NV_OWNERREAD. TPMA_NV_BIND does not appear in the spec anywhere. I told the AI that.
I apologize for the error in my previous response. You are correct that the TPMA_NV_BIND attribute does not appear in the TPM 2.0 specification.
To bind an encryption key to the value of a TPM NV index, you can use the TPM2_NV_DefineSpace command with the TPMA_NV_BIND attribute.
I'm not afraid of being unemployed in the near future.
[1] "Platform Configuration Registers" - a modern TPM has 24 of these. When something security sensitive happens, you generate a hash of that event and pass it to the TPM. The TPM appends that to an existing PCR value and then hashes that concatenated value and sets the PCR to that. This means the PCR value depends not only on the values provided, but also the order they're provided in. Various TPM operations can be made conditional on the PCR values meeting specific criteria.
 Here is another monthly update covering what I have been doing in the free software world during August 2020 (
Here is another monthly update covering what I have been doing in the free software world during August 2020 (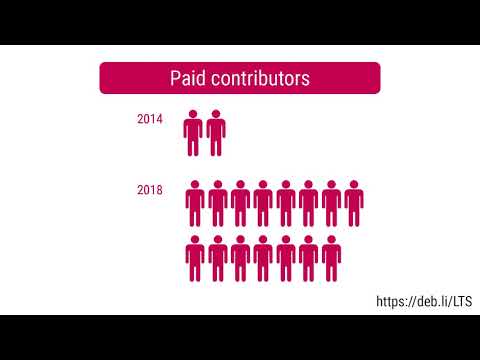

 Part of our
Part of our  Those people who overread the previous blog entry but are interested in samba, please test the 3.2.0~rc1 packages we have in experimental.
We still haven't decided whether we'll push to have it in lenny or not (Samba 3.2.0 should be released very very soon and the Samba Team pushes for us to have it in Debian lenny....which might need solving out issues induced by the move to GPLv3)....but it deserves as much testing as possible.
I think that it's safe to use it on "semi-production" machines (those machines you might already have using testing because you want bleeding edge software). So, please, given the very various ways to use samba, please help us and our upstream to test it.
The packages are in experimental, by the way.
Those people who overread the previous blog entry but are interested in samba, please test the 3.2.0~rc1 packages we have in experimental.
We still haven't decided whether we'll push to have it in lenny or not (Samba 3.2.0 should be released very very soon and the Samba Team pushes for us to have it in Debian lenny....which might need solving out issues induced by the move to GPLv3)....but it deserves as much testing as possible.
I think that it's safe to use it on "semi-production" machines (those machines you might already have using testing because you want bleeding edge software). So, please, given the very various ways to use samba, please help us and our upstream to test it.
The packages are in experimental, by the way.