Review:
The Truth, by Terry Pratchett
| Series: |
Discworld #25 |
| Publisher: |
Harper |
| Copyright: |
November 2000 |
| Printing: |
August 2014 |
| ISBN: |
0-06-230736-3 |
| Format: |
Mass market |
| Pages: |
435 |
The Truth is the 25th Discworld novel. Some reading order guides
group it loosely into an "industrial revolution" sequence following
Moving Pictures, but while there are
thematic similarities I'll talk about in a moment, there's no real plot
continuity. You could arguably start reading Discworld here, although
you'd be spoiled for some character developments in the early Watch
novels.
William de Worde is paid to write a newsletter. That's not precisely what
he calls it, and it's not clear whether his patrons know that he publishes
it that way. He's paid to report on news of Ankh-Morpork that may be of
interest of various rich or influential people who are not in
Ankh-Morpork, and he discovered the best way to optimize this was to write
a template of the newsletter, bring it to an engraver to make a plate of
it, and run off copies for each of his customers, with some minor
hand-written customization. It's a comfortable living for the estranged
younger son of a wealthy noble. As the story opens, William is dutifully
recording the rumor that dwarfs have discovered how to turn lead into
gold.
The rumor is true, although not in the way that one might initially
assume.
The world is made up of four elements: Earth, Air, Fire, and Water.
This is a fact well known even to Corporal Nobbs. It's also wrong.
There's a fifth element, and generally it's called Surprise.
For example, the dwarfs found out how to turn lead into gold by doing
it the hard way. The difference between that and the easy way is that
the hard way works.
The dwarfs used the lead to make a movable type printing press, which is
about to turn William de Worde's small-scale, hand-crafted newsletter into
a newspaper.
The movable type printing press is not unknown technology. It's banned
technology, because the powers that be in Ankh-Morpork know enough to be
deeply suspicious of it. The religious establishment doesn't like it
because words are too important and powerful to automate. The nobles and
the Watch don't like it because cheap words cause problems. And the
engraver's guild doesn't like it for obvious reasons. However, Lord
Vetinari knows that one cannot apply brakes to a volcano, and commerce
with the dwarfs is very important to the city. The dwarfs can continue.
At least for now.
As in
Moving Pictures, most of
The Truth is an idiosyncratic
speedrun of the social effects of a new technology, this time newspapers.
William has no grand plan; he's just an observant man who likes to write,
cares a lot about the truth, and accidentally stumbles into editing a
newspaper. (This, plus being an estranged son of a rich family, feels
very on-point for journalism.) His naive belief is that people want to
read true things, since that's what his original patrons wanted. Truth,
however, may not be in the top five things people want from a newspaper.
This setup requires some narrative force to push it along, which is
provided by a plot to depose Vetinari by framing him for murder. The most
interesting part of that story is Mr. Pin and Mr. Tulip, the people hired
to do the framing and then dispose of the evidence. They're a classic
villain type: the brains and the brawn, dangerous, terrifying, and willing
to do horrible things to people. But one thing Pratchett excels at is
taking a standard character type, turning it a bit sideways, and stuffing
in things that one wouldn't think would belong. In this case, that's
Mr. Tulip's deep appreciation for, and genius grasp of, fine art. It
should not work to have the looming, awful person with anger issues be
able to identify the exact heritage of every sculpture and fine piece of
goldsmithing, and yet somehow it does.
Also as in
Moving Pictures (and, in a different way,
Soul Music), Pratchett tends to
anthropomorphize technology, giving it a life and motivations of its own.
In this case, that's William's growing perception of the press as an
insatiable maw into which one has to feed words. I'm usually dubious of
shifting agency from humans to things when doing social analysis (and
there's a lot of social analysis here), but I have to concede that
Pratchett captures something deeply true about the experience of feedback
loops with an audience. A lot of what Pratchett puts into this book about
the problematic relationship between a popular press and the truth is
obvious and familiar, but he also makes some subtle points about the way
the medium shapes what people expect from it and how people produce
content for it that are worthy of
Marshall McLuhan.
The interactions between William and the Watch were less satisfying. In
our world, the US press is, with only rare exceptions, a thoughtless PR
organ for police propaganda and the
exonerative tense. Pratchett tackles that here... sort of. William
vaguely grasps that his job as a reporter may be contrary to the job of
the Watch to maintain order, and Vimes's ambivalent feelings towards
"solving crimes" push the story in that direction. But this is also
Vimes, who is clearly established as one of the good sort and therefore is
a bad vehicle for talking about how the police corrupt the press.
Pratchett has Vimes and Vetinari tacitly encourage William, which works
within the story but takes the pressure off the conflict and leaves
William well short of understanding the underlying politics. There's a
lot more that could be said about the tension between the press and the
authorities, but I think the Discworld setup isn't suitable for it.
This is the sort of book that benefits from twenty-four volumes of
backstory and practice. Pratchett's Ankh-Morpork cast ticks along like a
well-oiled machine, which frees up space that would otherwise have to be
spent on establishing secondary characters. The result is a lot of plot
and social analysis shoved into a standard-length Discworld novel, and a
story that's hard to put down. The balance between humor and plot is just
about perfect, the references and allusions aren't overwhelming, and the
supporting characters, both new and old, are excellent. We even get a
good Death sequence. This is solid, consistent stuff: Discworld as a
mature, well-developed setting with plenty of stories left to tell.
Followed by
Thief of Time in publication order, and later by
Monstrous Regiment in the vaguely-connected industrial revolution
sequence.
Rating: 8 out of 10
 This post describes how I m using
This post describes how I m using









 Dormitory room in Zostel Ernakulam, Kochi.
Dormitory room in Zostel Ernakulam, Kochi.
 Beds in Zostel Ernakulam, Kochi.
Beds in Zostel Ernakulam, Kochi.
 Onam sadya menu from Brindhavan restaurant.
Onam sadya menu from Brindhavan restaurant.
 Sadya lined up for serving
Sadya lined up for serving
 Sadya thali served on banana leaf.
Sadya thali served on banana leaf.
 We were treated with such views during the Wayanad trip.
We were treated with such views during the Wayanad trip.
 A road in Rippon.
A road in Rippon.
 Entry to Kanthanpara Falls.
Entry to Kanthanpara Falls.
 Kanthanpara Falls.
Kanthanpara Falls.
 A view of Zostel Wayanad.
A view of Zostel Wayanad.
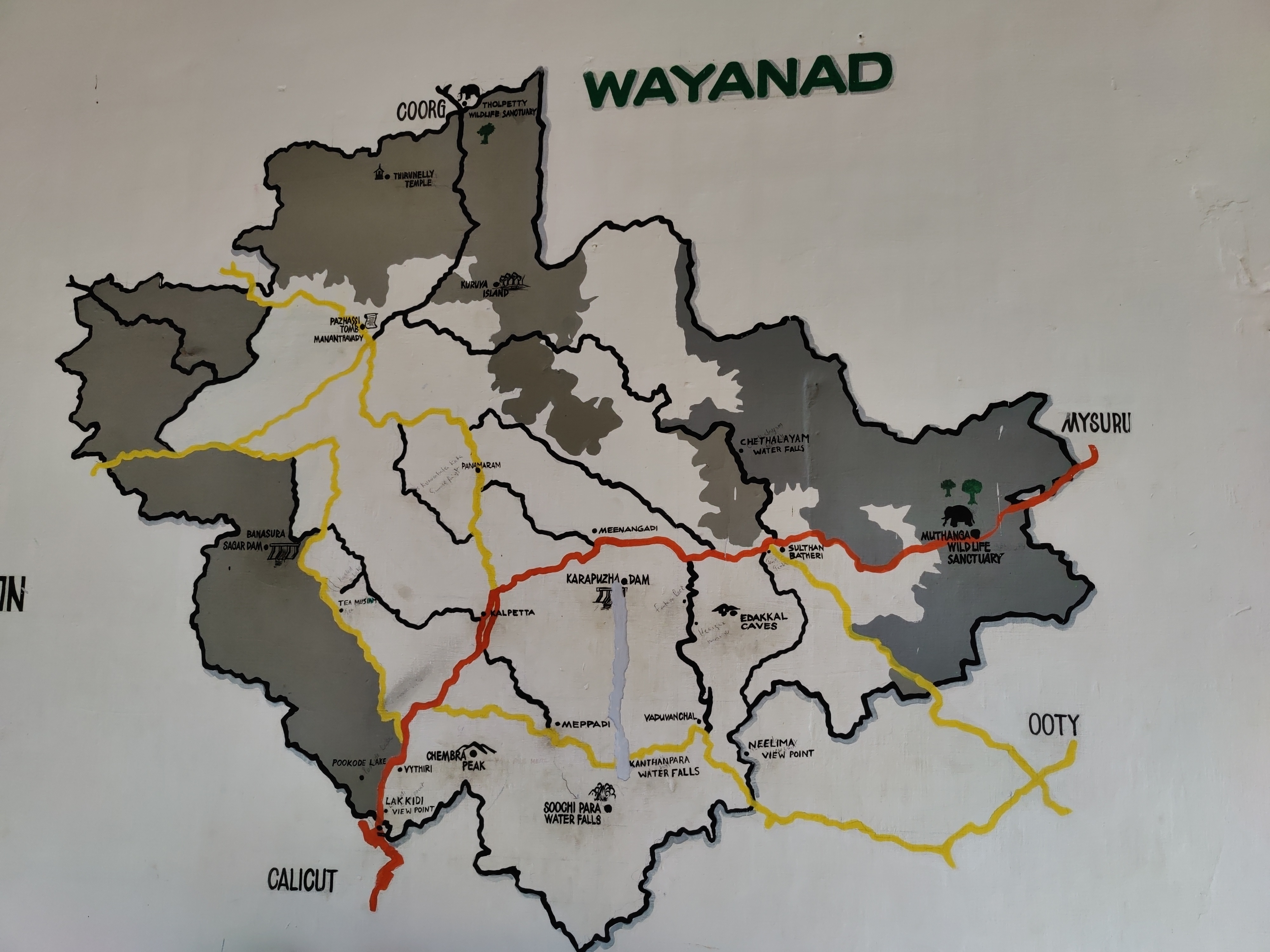 A map of Wayanad showing tourist places.
A map of Wayanad showing tourist places.
 A view from inside the Zostel Wayanad property.
A view from inside the Zostel Wayanad property.
 Terrain during trekking towards the Chembra peak.
Terrain during trekking towards the Chembra peak.
 Heart-shaped lake at the Chembra peak.
Heart-shaped lake at the Chembra peak.
 Me at the heart-shaped lake.
Me at the heart-shaped lake.
 Views from the top of the Chembra peak.
Views from the top of the Chembra peak.
 View of another peak from the heart-shaped lake.
View of another peak from the heart-shaped lake.

 QNAP TS-453mini product photo
QNAP TS-453mini product photo The logo for QNAP HappyGet 2 and Blizzard s StarCraft 2 side by side
The logo for QNAP HappyGet 2 and Blizzard s StarCraft 2 side by side Thermalright AXP120-X67, AMD Ryzen 5 PRO 5650GE, ASRock Rack X570D4I-2T, all assembled and running on a flat surface
Thermalright AXP120-X67, AMD Ryzen 5 PRO 5650GE, ASRock Rack X570D4I-2T, all assembled and running on a flat surface Memtest86 showing test progress, taken from IPMI remote control window
Memtest86 showing test progress, taken from IPMI remote control window Screenshot of PCIe 16x slot bifurcation options in UEFI settings, taken from IPMI remote control window
Screenshot of PCIe 16x slot bifurcation options in UEFI settings, taken from IPMI remote control window Internal image of Silverstone CS280 NAS build. Image stolen from
Internal image of Silverstone CS280 NAS build. Image stolen from  Internal image of Silverstone CS280 NAS build. Image stolen from
Internal image of Silverstone CS280 NAS build. Image stolen from  NAS build in Silverstone SUGO 14, mid build, panels removed
NAS build in Silverstone SUGO 14, mid build, panels removed Silverstone SUGO 14 from the front, with hot swap bay installed
Silverstone SUGO 14 from the front, with hot swap bay installed Storage SSD loaded into hot swap sled
Storage SSD loaded into hot swap sled TrueNAS Dashboard screenshot in browser window
TrueNAS Dashboard screenshot in browser window The final system, powered up
The final system, powered up
 Daniel Knowles Carmageddon: How Cars Make Life Worse and What to
Do About It is an entertaining, lucid, and well-written manifesto
(to borrow a term from the author) aiming to get us all thinking a bit
more about what cars do to society, and how to move on to a better
outcome for all.
The book alternates between historical context and background, lived
experience (as the author is a foreign correspondent who had the
opportunity to travel), and researched content. It is refreshingly free
of formalities (no endless footnotes or endnotes with references, though
I would have liked occassional references but hey we all went to school
long enough to do a bit of research given a pointer or two). I learned
or relearned a few things as I was for example somewhat unaware of the
air pollution (micro-particle) impact stemming from tires and brake
abrasions for which electronic vehicles do zilch, and for which the
auto-obesity of ever larger and heavier cars is making things
much worse. And some terms (even when re-used by Knowles) are clever
such bionic duckweed. But now you need to read the book to
catch up on it.
Overall, the book argues its case rather well. The author brings
sufficient evidence to make the formal guilty charge quite convincing.
It is also recent having come out just months ago, making current
figures even more relevant.
I forget the exact circumstance but I think I came across the author
in the context of our joint obsession with both Chicago and cycling (as
there may have been a link from a related social media post) and/or the
fact that I followed some of his colleagues at The Economist on
social media. Either way, the number of Chicago and MidWest references
made for some additional fun when reading the book over a the last few
days. And for me another highlight was the ode to Tokyo which I
wholeheartedly agree with: on my second trip to Japan I spent a spare
day cycling across the city as the AirBnB host kindly gave me access to
his bicycles. Great weather, polite drivers, moderate traffic, and just
wicked good infrastructure made me wonder why I did not see more
cyclists.
I have little to criticize beyond the lack of any references. The
repeated insistence on reminding us that Knowles comes from Birmingham
gets a little old by the fifth or sixth repetition. It is all a wee bit
anglo- or UK-centric. It obviously has a bit on France, Paris,
and all the recent success of Anne Hidalgo (who, when I was in graduate
school in France, was still a TV person rather than the very successful
mayor she is now) but then does not mention the immense (and well known)
success of the French train system which lead to a recent dictum to no
longer allow intra-Frace air travel if train rides of under 2 1/2 hours
are available which is rather remarkable. (Though in fairness that may
have been enacted once the book was finished.)
Lastly, the book appears to have
Daniel Knowles Carmageddon: How Cars Make Life Worse and What to
Do About It is an entertaining, lucid, and well-written manifesto
(to borrow a term from the author) aiming to get us all thinking a bit
more about what cars do to society, and how to move on to a better
outcome for all.
The book alternates between historical context and background, lived
experience (as the author is a foreign correspondent who had the
opportunity to travel), and researched content. It is refreshingly free
of formalities (no endless footnotes or endnotes with references, though
I would have liked occassional references but hey we all went to school
long enough to do a bit of research given a pointer or two). I learned
or relearned a few things as I was for example somewhat unaware of the
air pollution (micro-particle) impact stemming from tires and brake
abrasions for which electronic vehicles do zilch, and for which the
auto-obesity of ever larger and heavier cars is making things
much worse. And some terms (even when re-used by Knowles) are clever
such bionic duckweed. But now you need to read the book to
catch up on it.
Overall, the book argues its case rather well. The author brings
sufficient evidence to make the formal guilty charge quite convincing.
It is also recent having come out just months ago, making current
figures even more relevant.
I forget the exact circumstance but I think I came across the author
in the context of our joint obsession with both Chicago and cycling (as
there may have been a link from a related social media post) and/or the
fact that I followed some of his colleagues at The Economist on
social media. Either way, the number of Chicago and MidWest references
made for some additional fun when reading the book over a the last few
days. And for me another highlight was the ode to Tokyo which I
wholeheartedly agree with: on my second trip to Japan I spent a spare
day cycling across the city as the AirBnB host kindly gave me access to
his bicycles. Great weather, polite drivers, moderate traffic, and just
wicked good infrastructure made me wonder why I did not see more
cyclists.
I have little to criticize beyond the lack of any references. The
repeated insistence on reminding us that Knowles comes from Birmingham
gets a little old by the fifth or sixth repetition. It is all a wee bit
anglo- or UK-centric. It obviously has a bit on France, Paris,
and all the recent success of Anne Hidalgo (who, when I was in graduate
school in France, was still a TV person rather than the very successful
mayor she is now) but then does not mention the immense (and well known)
success of the French train system which lead to a recent dictum to no
longer allow intra-Frace air travel if train rides of under 2 1/2 hours
are available which is rather remarkable. (Though in fairness that may
have been enacted once the book was finished.)
Lastly, the book appears to have 
 A real sad state of affairs
A real sad state of affairs 

















 US-11604662-B2
US-11604662-B2 Two weeks ago, I had the chance to go see Cory Doctorow at my local independent
bookstore, in Montr al. He was there to present his latest essay, co-written
with Rebecca Giblin
Two weeks ago, I had the chance to go see Cory Doctorow at my local independent
bookstore, in Montr al. He was there to present his latest essay, co-written
with Rebecca Giblin Although Doctorow is known for his strong political stances, I have to say I'm
quite surprised by the quality of the research Giblin and he did for this book.
They both show a pretty advanced understanding of the market dynamics they look
at, and even though most of the solutions they propose aren't new or
groundbreaking, they manage to be convincing and clear.
That is to say, you certainly don't need to be an economist to understand or
enjoy this book :)
As I have mentioned before, the book heavily criticises monopolies, but also
monopsonies a market structure that has only one buyer (instead of one
seller). I find this quite interesting, as whereas people are often familiar
with the concept of monopolies, monopsonies are frequently overlooked.
The classic example of a monopsony is a labor market with a single employer:
there is a multitude of workers trying to sell their labor power, but in the
end, working conditions are dictated by the sole employer, who gets to decide
who has a job and who hasn't. Mining towns are good real-world examples of
monopsonies.
In the book, the authors argue most of the contemporary work produced by
creative workers (especially musicians and writers) is sold to monopsonies and
Although Doctorow is known for his strong political stances, I have to say I'm
quite surprised by the quality of the research Giblin and he did for this book.
They both show a pretty advanced understanding of the market dynamics they look
at, and even though most of the solutions they propose aren't new or
groundbreaking, they manage to be convincing and clear.
That is to say, you certainly don't need to be an economist to understand or
enjoy this book :)
As I have mentioned before, the book heavily criticises monopolies, but also
monopsonies a market structure that has only one buyer (instead of one
seller). I find this quite interesting, as whereas people are often familiar
with the concept of monopolies, monopsonies are frequently overlooked.
The classic example of a monopsony is a labor market with a single employer:
there is a multitude of workers trying to sell their labor power, but in the
end, working conditions are dictated by the sole employer, who gets to decide
who has a job and who hasn't. Mining towns are good real-world examples of
monopsonies.
In the book, the authors argue most of the contemporary work produced by
creative workers (especially musicians and writers) is sold to monopsonies and




