
Whilst I managed to read almost sixty books in 2016 here are ten of my favourites in no particular order.
Disappointments this year include Stewart Lee's
Content Provider (nothing like his stand-up), Christopher Hitchens'
And Yet (his best essays are already published) and Heinlein's
Stranger in a Strange Land (great exposition, bizarre conclusion).
The worst book I finished, by far, was Mark Edward's
Follow You Home.
 Animal QC
Gary Bell, QC
Animal QC
Gary Bell, QC
Subtitled
My Preposterous Life, this rags-to-riches story about a working-class boy turned eminent lawyer would be highly readable as a dry and factual account but I am compelled to include it here for its extremely entertaining style of writing.
Full of unsurprising quotes that take one unaware: would you really expect a now-Queen's Counsel to "heartily suggest that if you find yourself suffering from dysentery in foreign climes you do not medicate it with lobster thermidor and a bottle of Ecuadorian red?"
A real good yarn.
 So You've Been Publically Shamed
Jon Ronson
So You've Been Publically Shamed
Jon Ronson
The author was initially recommended to me by
Brad but I believe I started out with the wrong book. In fact, I even had my doubts about this one, prematurely judging from the title that it was merely cashing-in on a fairly recent internet phenomenon like his more recent
shallow take on Trump and the alt-Right but in the end I read
Publically Shamed thrice in quick succession.
I would particularly endorse the audiobook version: Ronson's deadpan drawl suits his writing perfectly.
 The Obstacle is the Way
Ryan Holiday
The Obstacle is the Way
Ryan Holiday
Whilst everyone else appears to be obligated to include Ryan's recent
Ego is the Enemy in their Best of 2016 lists I was actually taken by his earlier "introduction by stealth" to stoic philosophy.
Certainly not your typical self-help book, this is "a manual to turn to in troubling times".
Returning to this work at least three times over the year even splashing out on the audiobook at some point I feel like I learned a great deal, although it is now difficult to pinpoint exactly what. Perhaps another read in 2017 is thus in order
 Layer Cake
J.J. Connolly
Layer Cake
J.J. Connolly
To judge a book in comparison to the film is to do both a disservice, but reading the book of
Layer Cake really underscored just how well the film played to the strengths of that medium.
All of the aspects that would not have worked had been carefully excised from the screenplay, ironically leaving more rewarding "layers" for readers attempting the book. A parallel adaption here might be
No Country for Old Men - I would love to read (or write) a comparative essay between these two adaptions although McCarthy's novel is certainly the superior source material.
 Lying
Sam Harris
Lying
Sam Harris
I've absorbed a lot of Sam Harris's
uvre this year in the form of his books but moreover
via his compelling podcast. I'm especially fond of
Waking Up on spirituality without religion and would rank that as my favourite work of his.
Lying is a comparatively short read, more of a long essay in fact, where he argues that we can radically simplify our lives by merely telling the truth in situations where others invariably lie. Whilst it would take a brave soul to adopt his approach his case is superlatively well-argued and a delight to read.
 Letters from a Stoic
Seneca
Letters from a Stoic
Seneca
Great pleasure is to be found not only in keeping up an old and established friendship but also in beginning and building up a new one.
Reading this in a beautifully svelte hardback, I tackled a randomly-chosen letter per day rather than attempting to read it cover-to-cover. Breaking with a life-long tradition, I even decided to highlight sections in pen so I could return to them at ease.
I hope it's not too hackneyed to claim I gained a lot from "building up" a relationship with this book. Alas, it is one of those books that is too easy to recommend given that it might make one appear wise and learned, but if you find yourself in a slump, either in life or in your reading habits, it certainly has my approval.
 Solo: A James Bond Novel
William Boyd
Solo: A James Bond Novel
William Boyd
I must have read all of the canonical Fleming novels as a teenager and
Solo really rewards anyone who has done so. It would certainly punish anyone expecting a
Goldeneye or at least be a little too foreign to be enjoyed.
Indeed, its really a pastiche of these originals, both in terms of the time period, general tone (Bond is more somber; more vulnerable) and in various obsessions of Fleming's writing, such as the overly-detailed description of the gambling and dining tables. In this universe, 007's restaurant expenses probably contributed signifcantly to the downfall of the British Empire, let alone his waistline.
Bond flicking through a ornithological book at one point was a cute touch
 The Subtle Art of Not Giving A F*ck
Mark Manson
The Subtle Art of Not Giving A F*ck
Mark Manson
Certainly a wildcard to include here and not without its problems,
The Subtle Art is a curious manifesto on how to approach life. Whilst Manson expouses an age-old philosophy of grounding yourself and ignoring the accumulation of flatscreen TVs, etc. he manages to do so in a fresh and provocative "21st-centry gonzo" style.
Highly entertaining, at one point the author posits an alternative superhero ("Disappointment Panda") that dishes out unsolicited and uncomfortable truths to strangers before simply walking away: "You know, if you make more money, that s not going to make your kids love you," or: "What you consider friendship is really just your constant attempts to impress people."
Ouch.
 The Fourth Protocol
Frederick Forsyth
The Fourth Protocol
Frederick Forsyth
I have a crystal-clear memory from my childhood of watching a single scene from a film in the dead of night: Pierce Brosnan sets a nuclear device to detonate after he can get away but a double-crossing accomplice surreptitiously brings the timetable forward in order that the bomb also disposes of him
Anyway, at some point whilst reading
The Fourth Protocol it dawned on me that this was that book. I might thus be giving the book more credit due to this highly satisfying connection but I think it stands alone as a superlative political page-turner and is still approachable outside the machinations of the Cold War.
 The Partner
John Grisham
The Partner
John Grisham
After indulging in a bit too much non-fiction and an aborted attempt at
The Ministry of Fear, I turned to a few so-called lower-brow writers such as Jeffrey Archer, etc.
However, it was
The Partner that turned out to be a real page-turner for somewhat undefinable reasons. Alas, it appears the rest of the author's output is unfortunately in the same vein (laywers, etc.) so I am hesitant to immediately begin others but judging from various lists online I am glad I approached this one first.
 Shogun: The First Novel of the Asian saga
James Clavell
Shogun: The First Novel of the Asian saga
James Clavell
Despite its length, I simply couldn't resist returning to
Shogun this year although it did fatigue me to the point that I have still yet to commence on its sequel,
Tai-Pan.
Like any good musical composition, one is always rewarded by returning to a book and I took great delight in uncovering more symbolism throughout (such as noticing that one of the first words Blackthorne learns in Japanese is "truth") but also really savouring the tragic arcs that run throughout the novel, some beautiful phrases ("The day seemed to lose its warmth ") and its wistful themes of inevitability and karma.
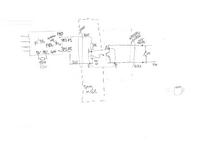
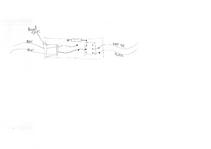 (click for diagram scans as pdfs).
The DigiSpark has just a USB tongue, which is very wobbly in a normal USB socket. I designed a 3D printed case which also had an approximation of the rest of the USB A plug. The plug is out of spec; our printer won t go fine enough - and anyway, the shield is supposed to be metal, not fragile plastic. But it fit in the USB PSU I was using, satisfactorily if a bit stiffly, and also into the connector for programming via my laptop.
Inside the coffee machine, there s the boundary between the original, coupled to mains, UI board, and the isolated low voltage of the microcontroller. I used a reasonably substantial cable to bring out the low voltage connection, past all the other hazardous innards, to make sure it stays isolated.
I added a drain power supply resistor on another of the GPIOs. This is enabled, with a draw of about 30mA, when the microcontroller is soon going to off / on cycle the coffee machine. That reduces the risk that the user will turn off the smart plug, and turn off the machine, but that the microcontroller turns the coffee machine back on again using the remaining power from USB PSU. Empirically in my setup it reduces the time from smart plug off to microcontroller stops from about 2-3s to more like 1s.
Optoisolator board (inside coffee machine) pictures
(Click through for full size images.)
(click for diagram scans as pdfs).
The DigiSpark has just a USB tongue, which is very wobbly in a normal USB socket. I designed a 3D printed case which also had an approximation of the rest of the USB A plug. The plug is out of spec; our printer won t go fine enough - and anyway, the shield is supposed to be metal, not fragile plastic. But it fit in the USB PSU I was using, satisfactorily if a bit stiffly, and also into the connector for programming via my laptop.
Inside the coffee machine, there s the boundary between the original, coupled to mains, UI board, and the isolated low voltage of the microcontroller. I used a reasonably substantial cable to bring out the low voltage connection, past all the other hazardous innards, to make sure it stays isolated.
I added a drain power supply resistor on another of the GPIOs. This is enabled, with a draw of about 30mA, when the microcontroller is soon going to off / on cycle the coffee machine. That reduces the risk that the user will turn off the smart plug, and turn off the machine, but that the microcontroller turns the coffee machine back on again using the remaining power from USB PSU. Empirically in my setup it reduces the time from smart plug off to microcontroller stops from about 2-3s to more like 1s.
Optoisolator board (inside coffee machine) pictures
(Click through for full size images.)


 Microcontroller board (in USB-plug-ish housing) pictures
Microcontroller board (in USB-plug-ish housing) pictures


 Implementation - software
I originally used the Arduino IDE, writing my program in C. I had a bad time with that and rewrote it in Rust.
The firmware is in a repository on Debian s gitlab
Results
I can now cause the coffee to start, from my phone. It can be programmed more than 12h in advance. And it stays warm until we ve drunk it.
UI is worse
There s one aspect of the original Morphy Richards machine that I haven t improved: the user interface is still poor. Indeed, it s now even worse:
To turn the machine on, you probably want to turn on the smart plug instead. Unhappily, the power button for that is invisible in its installed location.
In particular, in the usual case, if you want to turn it off, you should ideally turn off both the smart plug (which can be done with the button on it) and the coffee machine itself. If you forget to turn off the smart plug, the machine can end up being turned on, very briefly, a handful of times, over the next hour or two.
Epilogue
We had used the new features a handful of times when one morning the coffee machine just wouldn t make coffee. The UI showed it turning on, but it wouldn t get hot, so no coffee. I thought oh no, I ve broken it!
But, on investigation, I found that the machine s heating element was open circuit (ie, completely broken). I didn t mess with that part. So, hooray! Not my fault. Probably, just being inverted a number of times and generally lightly jostled, had precipitated a latent fault. The machine was a number of years old.
Happily I found a replacement, identical, machine, online. I ve transplanted my modification and now it all works well.
Bonus pictures
(Click through for full size images.)
Implementation - software
I originally used the Arduino IDE, writing my program in C. I had a bad time with that and rewrote it in Rust.
The firmware is in a repository on Debian s gitlab
Results
I can now cause the coffee to start, from my phone. It can be programmed more than 12h in advance. And it stays warm until we ve drunk it.
UI is worse
There s one aspect of the original Morphy Richards machine that I haven t improved: the user interface is still poor. Indeed, it s now even worse:
To turn the machine on, you probably want to turn on the smart plug instead. Unhappily, the power button for that is invisible in its installed location.
In particular, in the usual case, if you want to turn it off, you should ideally turn off both the smart plug (which can be done with the button on it) and the coffee machine itself. If you forget to turn off the smart plug, the machine can end up being turned on, very briefly, a handful of times, over the next hour or two.
Epilogue
We had used the new features a handful of times when one morning the coffee machine just wouldn t make coffee. The UI showed it turning on, but it wouldn t get hot, so no coffee. I thought oh no, I ve broken it!
But, on investigation, I found that the machine s heating element was open circuit (ie, completely broken). I didn t mess with that part. So, hooray! Not my fault. Probably, just being inverted a number of times and generally lightly jostled, had precipitated a latent fault. The machine was a number of years old.
Happily I found a replacement, identical, machine, online. I ve transplanted my modification and now it all works well.
Bonus pictures
(Click through for full size images.)

 edited 2023-11-26 14:59 UTC in an attempt to fix TOC links
edited 2023-11-26 14:59 UTC in an attempt to fix TOC links Em 2023 o tradicional
Em 2023 o tradicional 
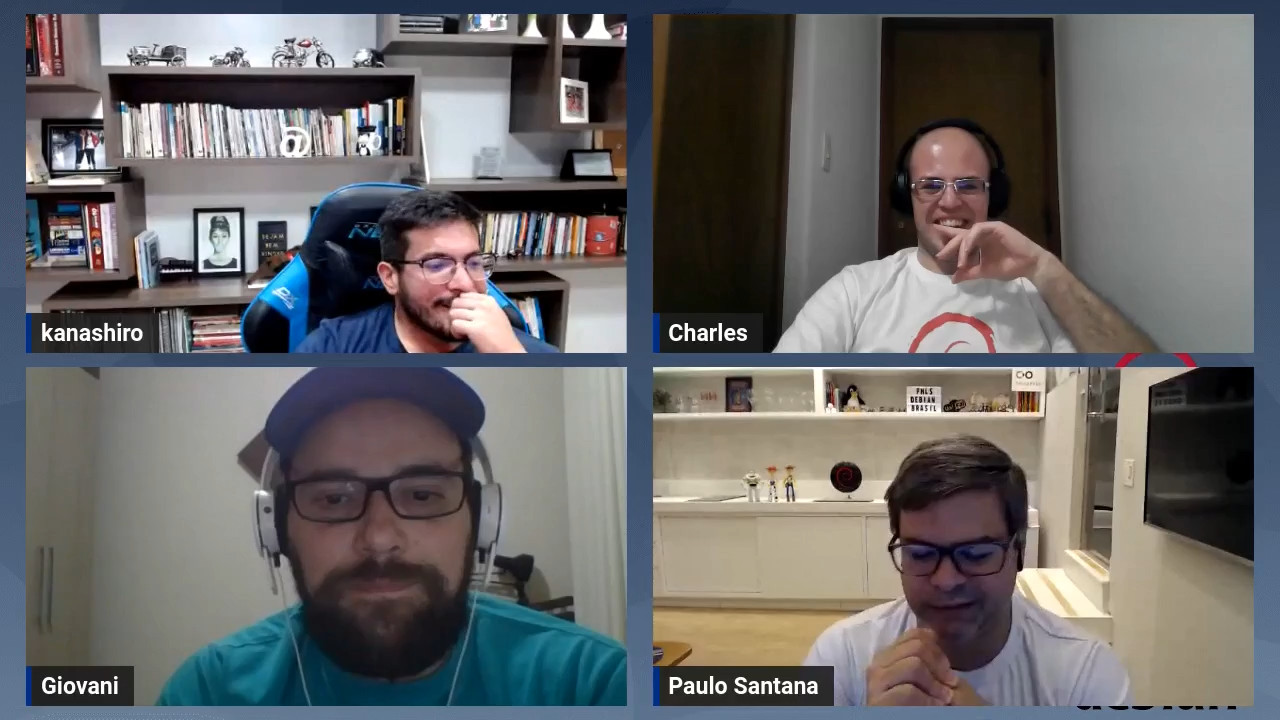

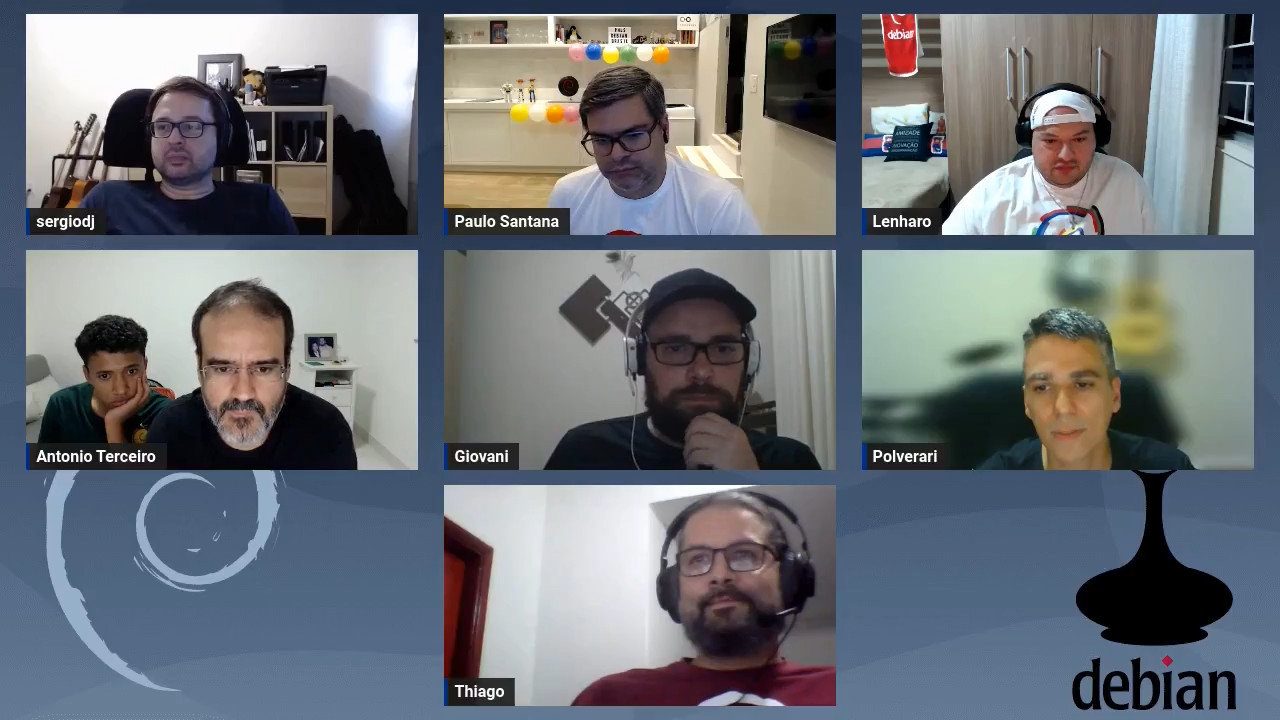
 V rias pessoas visitaram o estande e aquelas mais iniciantes (principalmente
estudantes) que n o conheciam o Debian, perguntavam do que se tratava o nosso
grupo e a gente explicava v rios conceitos como o que Software Livre,
distribui o GNU/Linux e o Debian propriamente dito. Tamb m recebemos pessoas
da comunidade de Software Livre brasileira e de outros pa ses da Am rica Latina
que j utilizavam uma distribui o GNU/Linux e claro, muitas pessoas que j
utilizavam Debian. Tivemos algumas visitas especiais como do Jon maddog Hall,
do Desenvolvedor Debian Emeritus Ot vio Salvador, do Desenvolvedor Debian
V rias pessoas visitaram o estande e aquelas mais iniciantes (principalmente
estudantes) que n o conheciam o Debian, perguntavam do que se tratava o nosso
grupo e a gente explicava v rios conceitos como o que Software Livre,
distribui o GNU/Linux e o Debian propriamente dito. Tamb m recebemos pessoas
da comunidade de Software Livre brasileira e de outros pa ses da Am rica Latina
que j utilizavam uma distribui o GNU/Linux e claro, muitas pessoas que j
utilizavam Debian. Tivemos algumas visitas especiais como do Jon maddog Hall,
do Desenvolvedor Debian Emeritus Ot vio Salvador, do Desenvolvedor Debian
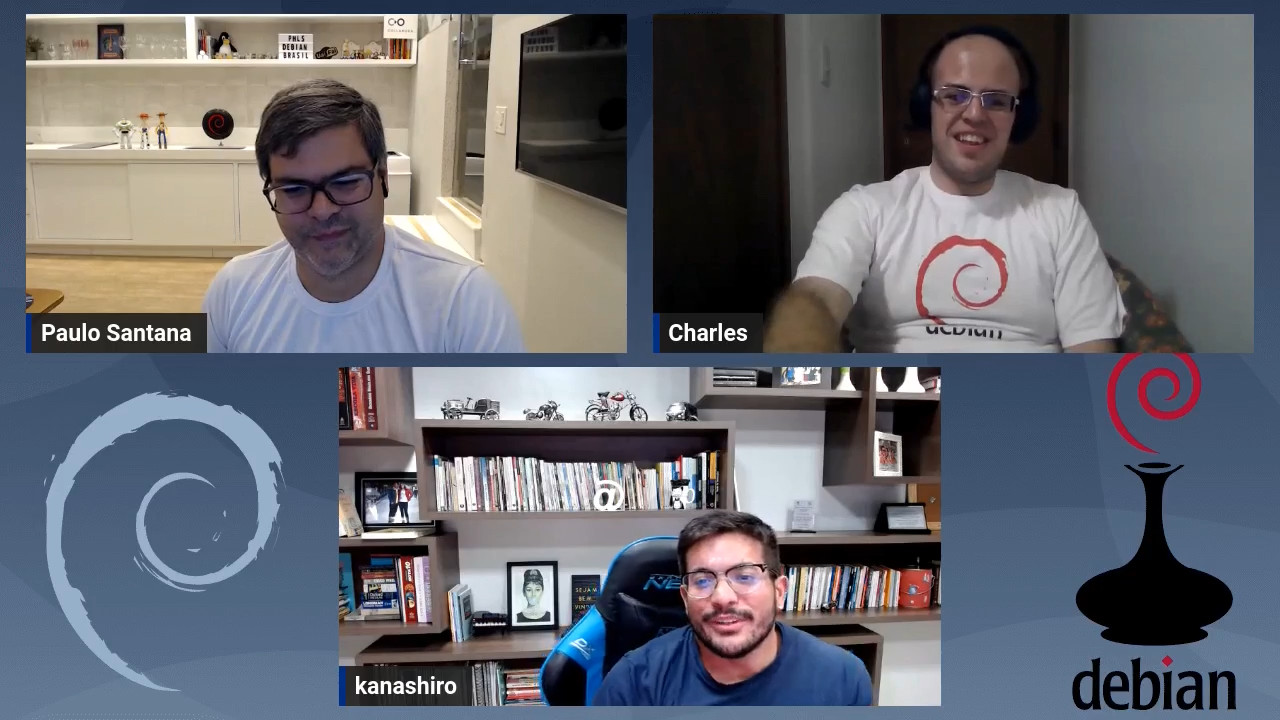
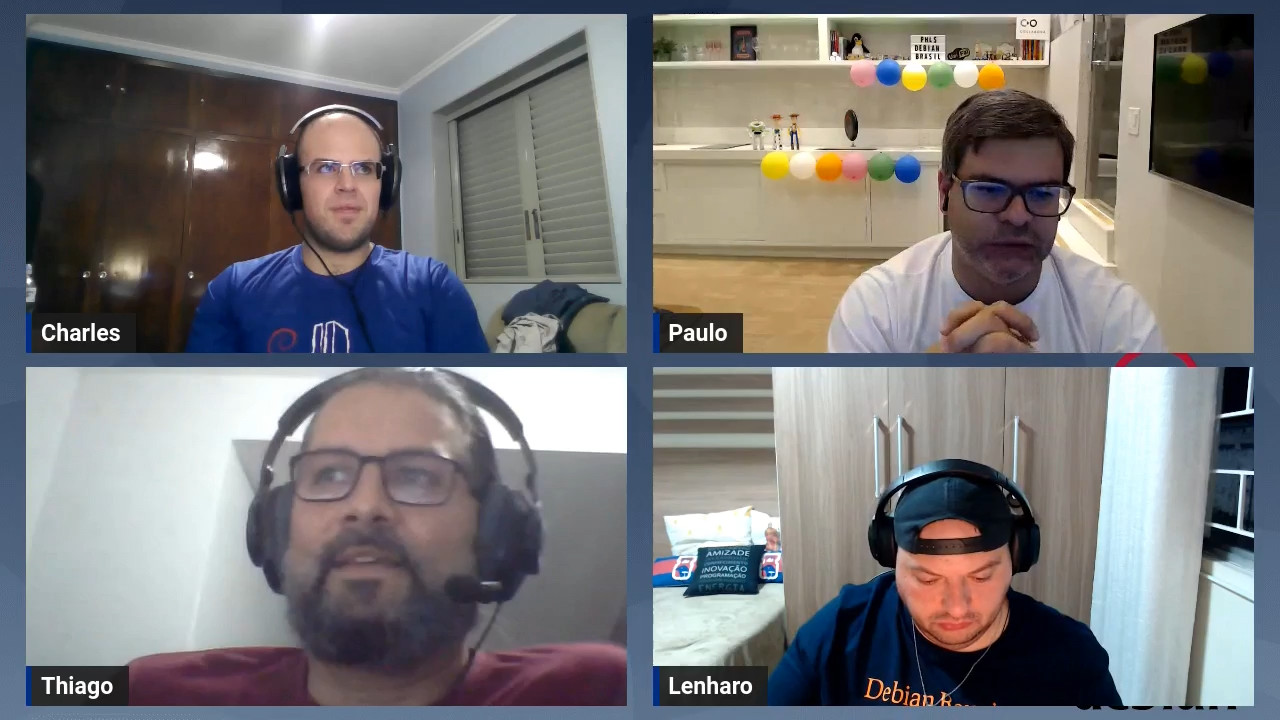
 Foto da esquerda pra direita: Leonardo, Paulo, Eriberto e Ot vio.
Foto da esquerda pra direita: Leonardo, Paulo, Eriberto e Ot vio.
 Foto da esquerda pra direita: Paulo, Fabian (Argentina) e Leonardo.
Al m de conversarmos bastante, distribu mos adesivos do Debian que foram
produzidos alguns meses atr s com o patroc nio do Debian para serem distribu dos
na DebConf22(e que haviam sobrado), e vendemos v rias
Foto da esquerda pra direita: Paulo, Fabian (Argentina) e Leonardo.
Al m de conversarmos bastante, distribu mos adesivos do Debian que foram
produzidos alguns meses atr s com o patroc nio do Debian para serem distribu dos
na DebConf22(e que haviam sobrado), e vendemos v rias

 Tamb m tivemos 3 palestras inseridas na programa o oficial do Latinoware.
Tamb m tivemos 3 palestras inseridas na programa o oficial do Latinoware.
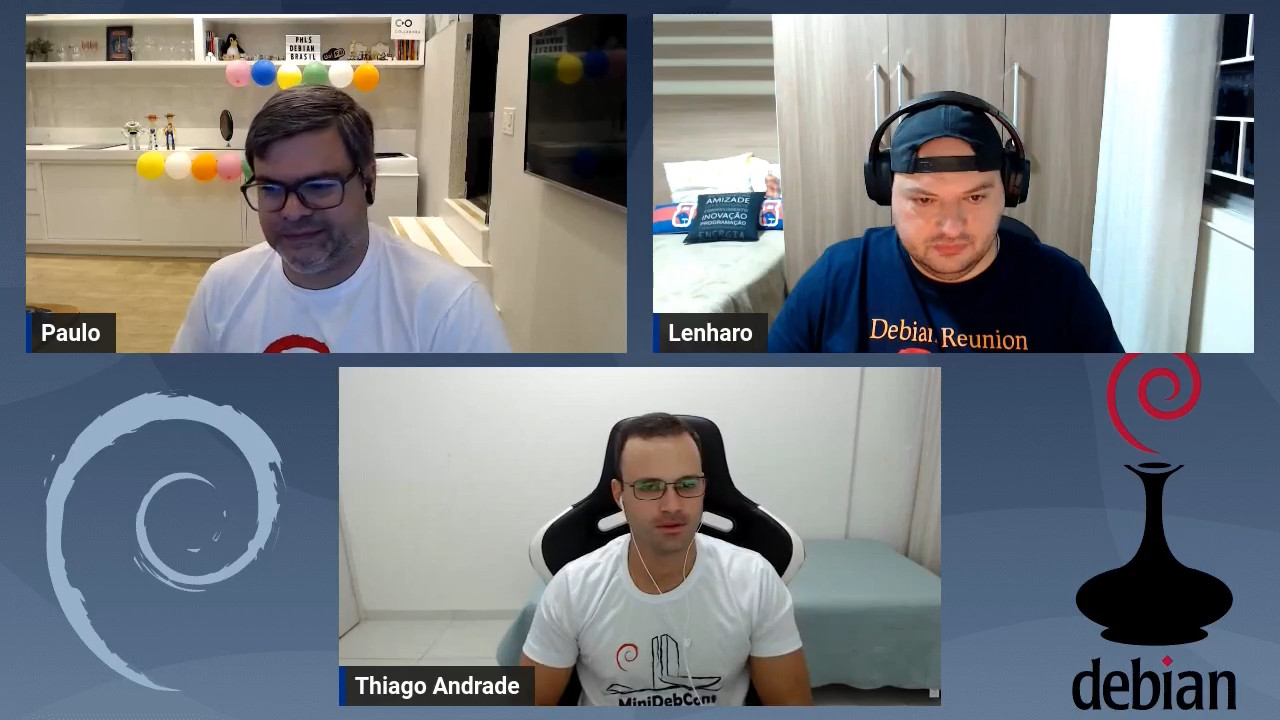
 Foto Paulo na palestra.
Agradecemos a organiza o do Latinoware por receber mais uma vez a comunidade
Debian e gentilmente ceder os espa os para a nossa participa o, e parabenizamos
a todas as pessoas envolvidas na organiza o pelo sucesso desse importante
evento para a nossa comunidade. Esperamos estar presentes novamente em 2023.
Agracemos tamb m ao Jonathan Carter por aprovar o suporte financeiro do Debian
para a nossa participa o no Latinoware.
Foto Paulo na palestra.
Agradecemos a organiza o do Latinoware por receber mais uma vez a comunidade
Debian e gentilmente ceder os espa os para a nossa participa o, e parabenizamos
a todas as pessoas envolvidas na organiza o pelo sucesso desse importante
evento para a nossa comunidade. Esperamos estar presentes novamente em 2023.
Agracemos tamb m ao Jonathan Carter por aprovar o suporte financeiro do Debian
para a nossa participa o no Latinoware.
 V rias pessoas visitaram o estande e aquelas mais iniciantes (principalmente
estudantes) que n o conheciam o Debian, perguntavam do que se tratava o nosso
grupo e a gente explicava v rios conceitos como o que Software Livre,
distribui o GNU/Linux e o Debian propriamente dito. Tamb m recebemos pessoas
da comunidade de Software Livre brasileira e de outros pa ses da Am rica Latina
que j utilizavam uma distribui o GNU/Linux e claro, muitas pessoas que j
utilizavam Debian. Tivemos algumas visitas especiais como do Jon maddog Hall,
do Desenvolvedor Debian Emeritus Ot vio Salvador, do Desenvolvedor Debian
V rias pessoas visitaram o estande e aquelas mais iniciantes (principalmente
estudantes) que n o conheciam o Debian, perguntavam do que se tratava o nosso
grupo e a gente explicava v rios conceitos como o que Software Livre,
distribui o GNU/Linux e o Debian propriamente dito. Tamb m recebemos pessoas
da comunidade de Software Livre brasileira e de outros pa ses da Am rica Latina
que j utilizavam uma distribui o GNU/Linux e claro, muitas pessoas que j
utilizavam Debian. Tivemos algumas visitas especiais como do Jon maddog Hall,
do Desenvolvedor Debian Emeritus Ot vio Salvador, do Desenvolvedor Debian
 Foto da esquerda pra direita: Leonardo, Paulo, Eriberto e Ot vio.
Foto da esquerda pra direita: Leonardo, Paulo, Eriberto e Ot vio.
 Foto da esquerda pra direita: Paulo, Fabian (Argentina) e Leonardo.
Al m de conversarmos bastante, distribu mos adesivos do Debian que foram
produzidos alguns meses atr s com o patroc nio do Debian para serem distribu dos
na DebConf22(e que haviam sobrado), e vendemos v rias
Foto da esquerda pra direita: Paulo, Fabian (Argentina) e Leonardo.
Al m de conversarmos bastante, distribu mos adesivos do Debian que foram
produzidos alguns meses atr s com o patroc nio do Debian para serem distribu dos
na DebConf22(e que haviam sobrado), e vendemos v rias

 Tamb m tivemos 3 palestras inseridas na programa o oficial do Latinoware.
Tamb m tivemos 3 palestras inseridas na programa o oficial do Latinoware.
 Foto Paulo na palestra.
Agradecemos a organiza o do Latinoware por receber mais uma vez a comunidade
Debian e gentilmente ceder os espa os para a nossa participa o, e parabenizamos
a todas as pessoas envolvidas na organiza o pelo sucesso desse importante
evento para a nossa comunidade. Esperamos estar presentes novamente em 2023.
Agracemos tamb m ao Jonathan Carter por aprovar o suporte financeiro do Debian
para a nossa participa o no Latinoware.
Foto Paulo na palestra.
Agradecemos a organiza o do Latinoware por receber mais uma vez a comunidade
Debian e gentilmente ceder os espa os para a nossa participa o, e parabenizamos
a todas as pessoas envolvidas na organiza o pelo sucesso desse importante
evento para a nossa comunidade. Esperamos estar presentes novamente em 2023.
Agracemos tamb m ao Jonathan Carter por aprovar o suporte financeiro do Debian
para a nossa participa o no Latinoware.
 I was shocked to learn today that Richard Stallman has been reinstated as a
member of the board of the Free Software Foundation. I think this is plain
inappropriate, but I cannot see how anyone who doesn t think that could fail
to see the reinstatement as counterproductive. As Bradley M. Kuhn
I was shocked to learn today that Richard Stallman has been reinstated as a
member of the board of the Free Software Foundation. I think this is plain
inappropriate, but I cannot see how anyone who doesn t think that could fail
to see the reinstatement as counterproductive. As Bradley M. Kuhn 









 Welcome to the nineth post in the recognisably rancid R randomness series, or
Welcome to the nineth post in the recognisably rancid R randomness series, or  Here is my monthly update covering what I have been doing in the free software world during July 2017 (
Here is my monthly update covering what I have been doing in the free software world during July 2017 ( Since the question popped here and there, I'll post a short blog post about the issue right now so there's a reference somewhere.
As you may know, Brad Spengler (spender) and the Pax Team recently
Since the question popped here and there, I'll post a short blog post about the issue right now so there's a reference somewhere.
As you may know, Brad Spengler (spender) and the Pax Team recently  Welcome to gambaru.de. Here is my monthly report that covers what I have been doing for Debian. If you re interested in Java, Games and LTS topics, this might be interesting for you.
Debian Games
Welcome to gambaru.de. Here is my monthly report that covers what I have been doing for Debian. If you re interested in Java, Games and LTS topics, this might be interesting for you.
Debian Games











 Hi,
I am in two minds of what to write about Doha. My job has been vastly simplified by a friend when he shared with me
Hi,
I am in two minds of what to write about Doha. My job has been vastly simplified by a friend when he shared with me 
