
What happened in the
reproducible
builds effort this week:
Toolchain fixes
- Niels Thykier uploaded debhelper/9.20151004 which exports SOURCE_DATE_EPOCH when running
dh_auto_* (patch by Dhole). dh now also calls dh_strip_nondeterminism during build (patch by Andrew Ayer). The only remaining change regarding reproducibility in the custom debhelper is related to mtimes in data.tar which might be fixed directly in dpkg instead.
- Niels Thykier made another upload of debhelper/9.20151005 the next day to sort Build IDs added by
dh_strip in control files.
Scott Kitterman
fixed an
issue with non-deterministic Depends generated by
dh-python identified by Santiago Vila and Chris Lamb.
Lunar
updated the patch against
dpkg which makes the order of files in
control.tar.gz deterministic using the new
--sort=name option available in GNU Tar 1.28.
josch released sbuild version 0.66.0-1 with several fixes and improvements. The most notable one for
reproducible builds is the new
--build-path option and
$build_path configuration variable added by akira which allows to
explicitly chose a given build path.
Reiner Herrmann wrote a new
patch for
dh-systemd to sort the list of unit files in the generated maintainer scripts.
Packages fixed
The following packages became reproducible due to changes in their
build dependencies:
aoeui,
apron,
camlmix,
cudf,
findlib,
glpk-java,
hawtjni,
haxe,
java-atk-wrapper,
llvm-py,
misery,
mtasc,
ocamldsort,
optcomp,
spamoracle.
The following packages became reproducible after getting fixed:
Some uploads fixed some reproducibility issues but not all of them:
Untested
Patches submitted which have not made their way to the archive yet:
reproducible.debian.net
ProfitBricks once again increased their support for reproducible builds in Debian and in other free software projects by adding 58 new cores and 138 GiB of RAM to the already existing setup. Two new
amd64 build nodes and 16 new
amd64 build jobs have been added which doubles the build capacity per day and allows us to spot many kind of problems earlier. The size of the
tmpfs where builds are performed has also been increased from 70 to 200 GiB on all
amd64 build nodes. Huge
thanks!
When examining a package, a link now points to a table listing all previous recorded tests for the same package. (Mattia) The menu on the package pages has also been improved. (h01ger)
Packages in the
depwait state are now rescheduled automatically after five days. (h01ger)
Links to documentation and other projects being tested have been made more visible on the
landing page. (h01ger)
To reduce noise on the team IRC channel five different types of notifications have been turned into mail notifications. The remaining ones have been shortened and the status changes have been limited to
unstable and
experimental. (h01ger)
Maintainer notifications about status changes in a package will only be sent out once per day, and not on each status change. (h01ger)
diffoscope development
Some more experiments of concurrent processing have been made. None were good and reliable enough to be shared, though.
Package reviews
48
reviews have been removed, 189 added and 23 updated this week.
9 FTBFS bugs were reported by Chris Lamb.
Misc.
h01ger met with Levente Polyak to discuss testing Arch Linux on Debian continuous test system with an easily extensible framework. The idea is to also allow testing of other distributions, and provide a nice package based view like the one for Debian.








 After many years of effort, I am happy to announce that
After many years of effort, I am happy to announce that 










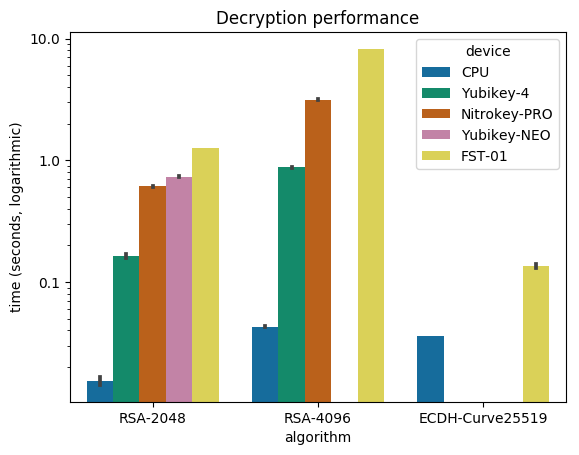
 What happened in the
What happened in the 


 I just released sbuild 0.66.0-1 into unstable. It fixes a whopping 30 bugs!
Thus, I'd like to use this platform to:
I just released sbuild 0.66.0-1 into unstable. It fixes a whopping 30 bugs!
Thus, I'd like to use this platform to:
